Trojan.FakeAv.QF
FakeAv is a new virus that infects computers released on 18th aug,09..... A rogue antivirus program called "Total Security 2009" that runs at system startup. A desktop shortcut and a Start menu entry are added by some variants.
These threats arrive mainly via spammed email messages that contain a link to a bogus celebrity video scandal, although the said link is also circulating in instant messaging applications and private messages in social networking Web sites.
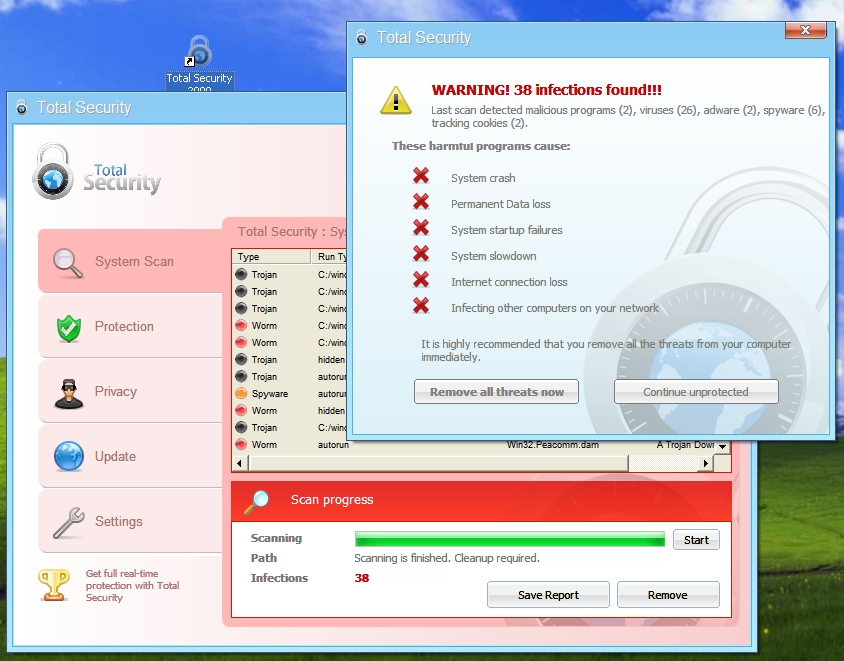
"Total Security 2009" is quite aggressive in forcing the user to register. New processes are declared to be infected and killed instantly.this virus causes low damage and medium spreading,but involves huge amount of interruptions.
BitDefender is probably the only antivirus till date which is able to detect it,but does not remove.Removal involves a lot of overheads.It leaves no traces where it gets installed and is almost untraceble.
1: close unnecessary services by using minimum services option at startup,coz this FakeAv starts during boot time.
2: scan with bitdefender and quarantine
3: go to C:\Documents and Settings\All Users\Application Data\17439374 and manually delete 17439374.exe
ur done........restart ur computer and ur virus free
A pseudo-scan starts and the same hardcoded detections are presented to the user, regardless of the state of the system.